Data processing is being revolutionized by edge computing. Devices managing data near the user handle data instead of sending it to massive data centers. Latency is reduced, and speed is improved. Edge computing brings them new security risks. The security concerns, attack types, countermeasures, and well-known methods used to protect edge computing systems are covered in this article.
Covered Contents
ToggleOverview
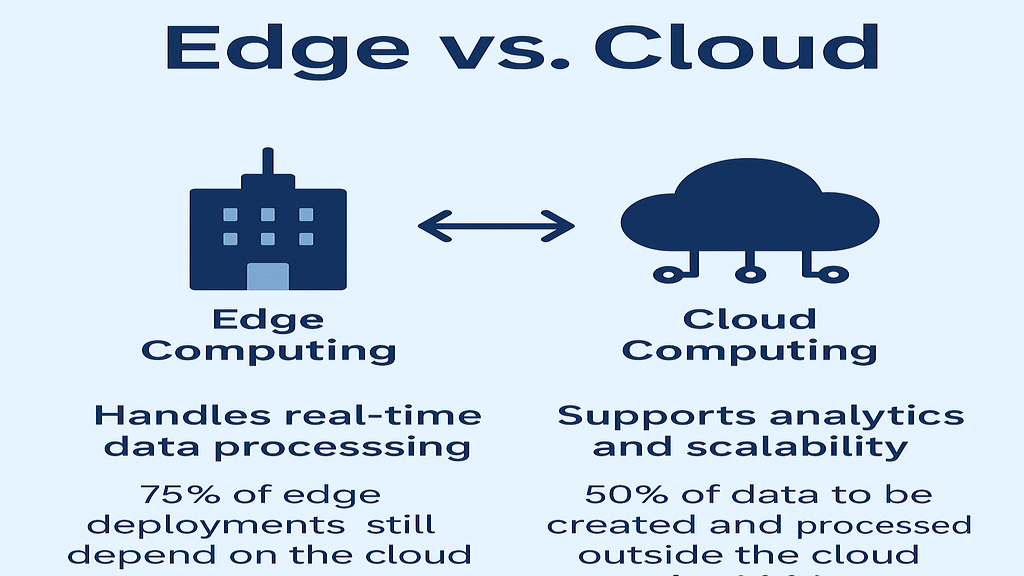
Edge computing brings processing closer to data sources. Nearby servers, sensors, and intelligent gadgets manage data near the edge. When quick judgments are crucial, the configuration is useful. For example, instant answers are used in medical monitors and autonomous cars.
Despite its many benefits, distributed edge computing also presents a large attack surface. Every device could be a weak point because there are so many of them in so many locations. If security isn’t good enough, cyber attackers can then target these weaknesses.
Businesses must implement strong security measures and advanced algorithms to fully utilize edge computing’s promise. These features—which include intrusion detection, safe authentication, and lightweight encryption—are designed to be implemented on devices with constrained processing power.
Edge Computing Security Concerns
The security of edge computing settings is fraught with difficulties. Due to the decentralized architecture, one of the main issues is the lack of a central location for security administration. Let’s talk about a few common edge computing security issues:
1. Increased Attack Surface
Extended Assault Surface Edge systems make use of numerous devices and nodes. Every additional device increases the likelihood of an intrusion. Edge devices are dispersed over numerous sites, in contrast to centralized cloud systems, where security is managed centrally. The network as a whole is more challenging to monitor and secure because of this heterogeneity.
2. Scarce Resources
Most edge devices are low-processing, low-memory, and power-constrained devices. Therefore, it is impossible to execute heavy security algorithms without causing the device’s performance to deteriorate. Instead, it is necessary to use lightweight security techniques.
3. Physical Security
Typically, edge devices are placed in less secure or public areas. They could be set up on production floors or in isolated locations. Anyone with physical access can steal information or assault hardware. These configurations are vulnerable to physical attacks.
4. Firmware Weaknesses
Software on several devices may contain problems. Additionally, out-of-date firmware may expose weaknesses that hackers might exploit. To prevent unwanted changes, secure boot and upgrades are essential.
5. Weaknesses in the Network
Data frequently moves between cloud computing and edge devices. Information is vulnerable to tampering or interception when it is moved. Data breaches can be caused by weak encryption or insecure protocols.
6. Variable Environments
Devices with diverse designs and vendors are used in edge computing. Because of this variety, it is difficult to create one-size-fits-all solutions and implement consistent security standards.
Common Types of Attacks on Edge Computing
Cybercriminals employ various methods to target edge systems, and the first line of defense against these attacks is awareness.
Physical Attacks
An attacker can physically steal or tamper with an edge device, potentially leading to malware infiltration or data theft. These threats can be mitigated with tamper detection sensors and robust physical security measures.
Attacks via Firmware and Software
Malicious code can be delivered through vulnerabilities in the operating system or firmware. Attackers may exploit these weaknesses to install backdoors or bypass secure boot processes. Regular system updates and secure boot procedures are essential in preventing such attacks.
Network Attacks
Traffic between devices can be intercepted. Attackers may use man-in-the-middle attacks to intercept or manipulate this traffic. Moreover, Distributed Denial-of-Service (DDoS) attacks may flood edge nodes with traffic, causing service disruption.
Data Poisoning and Model Extraction
Malicious data can be injected by the attackers in machine learning-based edge systems to spoil training processes, a process named data poisoning. They may further try to retrieve sensitive models in model extraction attacks, allowing them to be used for further attacks. These risks can compromise the integrity of the data and downsize model quality.
Adversarial Machine Learning Attacks
Attackers can develop adversarial examples that look legitimate to humans but mislead machine learning models to make wrong predictions. These kinds of attacks have the potential to seriously interfere with AI systems installed on edge devices, resulting in wrong decisions.
Byzantine Attacks in Federated Learning
Federated learning enables a number of edge devices to jointly train models without the sharing of raw data. In Byzantine attacks, however, malicious devices might provide misleading updates that poison the global model. Strong aggregation techniques need to be implemented too, to counteract this threat.
Edge Security Defense Techniques
Defending edge computing systems requires a multi-layered approach. Some possible defense tactics are listed below.
Lightweight Cryptography
For devices with low resources, legacy encryption techniques could be too complicated. The ideal protocols for the edge are lightweight ones like TinyECC, ChaCha20-Poly1305, and AES-128-GCM. Without using a lot of processing resources, they encrypt data both in transit and at rest.
Robust Access Control and Authentication
Use strong authentication methods to verify each user and device. Digital certificates (based on RSA or ECC) and multi-factor authentication (MFA) guarantee that only reliable users and devices can access the network. Edge computing benefits most from zero-trust architecture, which never trusts anyone, not even within the network.
Firmware Integrity and Secure Boot
A device loading trustworthy firmware is ensured by secure boot. This is carried out using a measured boot, which generates a boot record that can be verified. Firmware integrity can be verified using digital signatures and hash techniques (like SHA-256). Patching known vulnerabilities requires regular upgrades.
Segmenting networks
Divide the network into discrete, manageable segments. If one of the parts is compromised, this limits the attacker’s range of motion. For example, lateral movement is prevented by separating IoT devices from central servers. To reduce risk, micro-segmentation can even be carried out in small networks.
Intrusion Detection and Prevention Systems (IDPS)
Edge devices can install lightweight intrusion detection software that observes device and network traffic behavior. Machine learning techniques can be employed to identify real-time anomalies. Automated response systems can then block or isolate dubious behavior.
Containerization and Virtualization
Applications are separated from hardware through the virtualization of edge nodes. This limits the impact of an application that has been compromised. Technologies that protect sensitive data while processing include secure enclaves and trusted execution environments (TEEs).
Distributed ledgers and blockchain technology
Blockchain technology can provide an unchangeable record of data exchanges and transactions. Blockchain helps with data and device authenticity verification in edge computing. Access control across a decentralized network and secure key management are more applications of blockchain.
Techniques for Active Defense and Deception
Active defense refers to actions that increase the cost to the attackers. Attackers are misled, and their progress is slowed by techniques including changing target defenses, decoy systems, and honeypots. They also provide helpful details about attack strategies.
Key Edge Computing Security Algorithms
Edge computing systems are protected by a suite of algorithms. The following is a list of some of the main algorithms and methods used:
Algorithms for light-weight encryption
AES-128-GCM: Provides strong encryption with little resource usage. Ideal for both moving and stationary data.
ChaCha20-Poly1305: A good substitute, especially for systems without AES hardware capability.
TinyECC: An algorithm for light elliptic curve cryptography that can be used in low-end devices for key exchange and authentication.
SPONGENT: When traditional hashes like SHA-256 are too demanding, SPONGENT, a lightweight hash function, can be used.
These algorithms have been chosen because they strike a balance between efficiency and security, allowing even low-end devices to protect their data without suffering significant performance costs.
Digital Signatures and Public Key Infrastructure (PKI)
RSA and ECC: Utilized for secure key exchange and digital signatures. ECC is used in most edge environments because it has lower computational needs and smaller key sizes.
SHA-256/SHA-3: Hashing algorithms employed to assure data integrity as well as digital signatures.
They assist in the creation of trust by confirming that data is from an authenticated source and hasn’t been altered.
Firmware Verification Algorithms and Secure Boot
SHA-256/SHA-3: Again, these are used to compute a firmware hash on bootup.
Digital signatures: To ensure that firmware upgrades are genuine and unaltered, digital signatures are used.
Secure boot ensures that the firmware and operating system are not altered before the device starts up for normal operations.
Algorithms for Intrusion Detection Detection
Models for Machine Learning: Algorithms for clustering and anomaly detection help monitor unusual activity on devices or networks. Traffic or activity that deviates from a regular pattern can be identified using these models.
Signature-Based Detection: Rapidly detects malicious activity by using known attack patterns.
In dynamic edge situations, these algorithms’ real-time monitoring and quick response capabilities are essential.
Sturdy Aggregation in Federated Education
Strong gradient aggregation rules in federated learning offer defense against Byzantine attacks. The algorithms ensure that a few rogue devices that deliver incorrect updates won’t have an excessive impact on the central model.
Post-Quantum Cryptography
The development of quantum computing may make traditional encryption techniques obsolete. The goal of post-quantum cryptography is to create algorithms that can resist quantum attacks. For example, a recent area with encouraging outcomes is lattice-based cryptography.
Case Studies and Real-World Applications
Let us examine two instances that illustrate the implementation of these defense mechanisms and algorithms in actual edge computing systems.
Case Study 1: Safeguarding Smart Cities
Many sensors and Internet of Things devices are used in smart cities to monitor public safety, energy use, and transportation. To manage real-time data, hundreds of edge devices were set up in a big metropolis. The following actions were taken by the city:
Network segmentation is used to keep central data systems and public sensors apart.
Using digital certificates for strong authentication ensures that only reliable devices exchange data.
Secure boot procedures and regular firmware updates are used to confirm the integrity of the device.
As a result, the city was able to protect individuals’ privacy and significantly reduce the risk of cyberattacks.
Case Study 2: Security of Industrial IoT
A single IoT device was compromised in one manufacturing company, nearly bringing down the entire production process. To address this, the company implemented to:
Zero Trust model, which by default did not trust any device.
Used AES-128-GCM and TinyECC, two lightweight cryptography techniques, to send encrypted data across devices.
Installed machine learning-based intrusion detection systems (IDS) to look for network irregularities.
The organization was able to promptly identify and quarantine the impacted equipment and resume manufacturing without any disruptions because of these procedures.
Future Trends in Edge Computing Security
The field of edge computing security is evolving. The landscape will continue to change due to new challenges and technology. Among the trends to watch out for are:
Increased Use of Machine Learning and AI
Security systems powered by AI will proliferate. To anticipate and respond to attacks more quickly than human teams alone, these systems will process massive amounts of data in real time. This includes automated response systems as well as anomaly detection.
Post-Quantum Cryptography Development
Quantum-resistant algorithms will become more and more necessary as quantum computing develops. Already, Cloudflare is moving toward post-quantum cryptography. In the edge domain, the application of post-quantum solutions, including those based on lattices, will increase.
Hardware Security Progress
With the advent of confidential computing and trusted execution environments (TEEs), security at the hardware level will be enhanced. TEEs ensure that data is processed in protected environments, minimizing the chances of attacks at the software level. This will be particularly crucial for sensitive edge applications.
Improved Active Defense Actions
Edge networks will increasingly incorporate active defense tactics, such as moving target defense and deception methods (like honeypots). In addition to preventing assaults, these steps also collect information about how attacks are carried out, which aids in improving security procedures.
Regulation and Standardization
As edge computing becomes more widely used, standard security frameworks and laws will be created. These will help ensure that the measures are consistent across devices and sectors and force the companies to implement best practices.
In conclusion
Imagine driverless cars making judgments in milliseconds or smart houses reacting instantly as edge computing speeds up data processing by doing it locally. However, speed comes at a price: most scattered equipment (sensors, cameras) lack built-in security measures, making them prime targets for hackers. The answer? Multi-layered protections include network “quarantines” to trap breaches, strict identity verification, AI-based threat detection, and rapid encryption (AES-128-GCM). Cities are already using these tactics to fend off ransomware, and manufacturers are avoiding shutdowns. Tomorrow’s armor? Security built into hardware circuits, quantum-resistant cryptography, and AI forecasting attacks. Safety is a dash, not a box to check. Work more efficiently, evolve swiftly, and build a castle-like defense system. If we treat edge computing like a gem, its future will be bright.


2 thoughts on “Mitigating Security Challenges in Edge Computing: Attacks, Defense Strategies, and Algorithms”